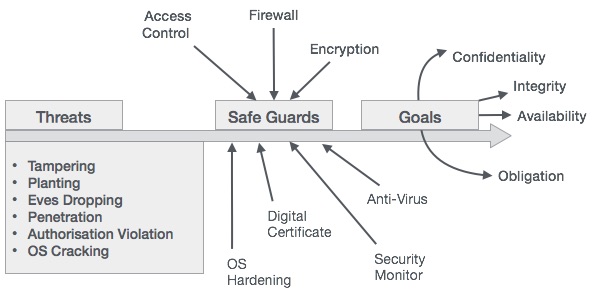
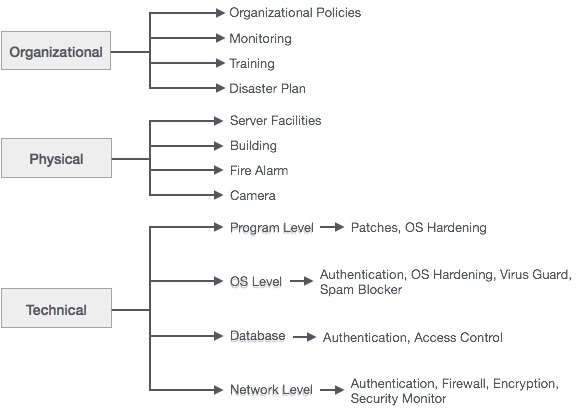
There are three points to look after in order to ensure security −
- Confidentiality − Unauthorized disclosure of data
- Integrity − Unauthorized modification of data
- Availability − Denial of service (a lack of availability of computing resources)
In SAP runtime environment, both application security and unauthorized system access to SAP have to be controlled. The user accounts defined for users in the SAP runtime environment are secured by roles that grant authorizations to them. SAP authorizations control access to transactions (Business Process Activities), or what can be performed within a specific business process step by −
- Keeping unauthorized persons out of the system
- Keeping people out of places where they should not be
- Safeguarding the data from damage or loss